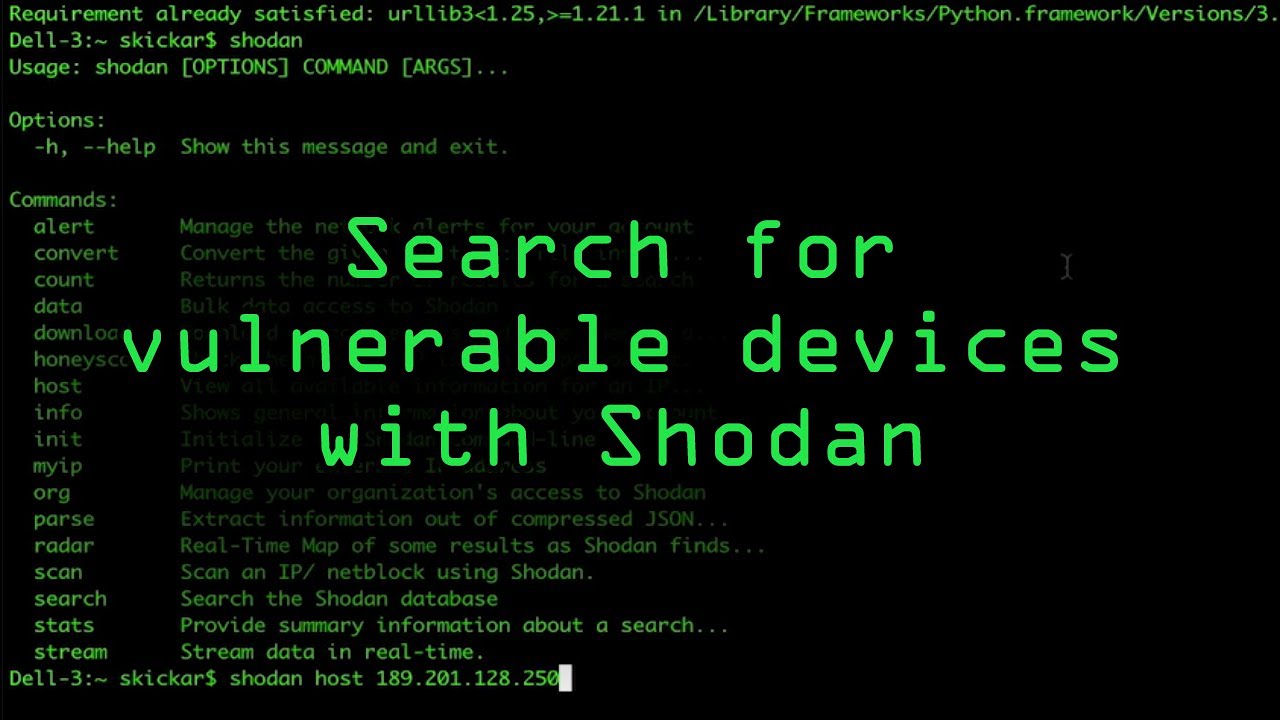
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

PenTest Edition: Using Shodan to Locate Internet-Connected Devices (Webcams, Servers, Routers, and More) – The Cybersecurity Man
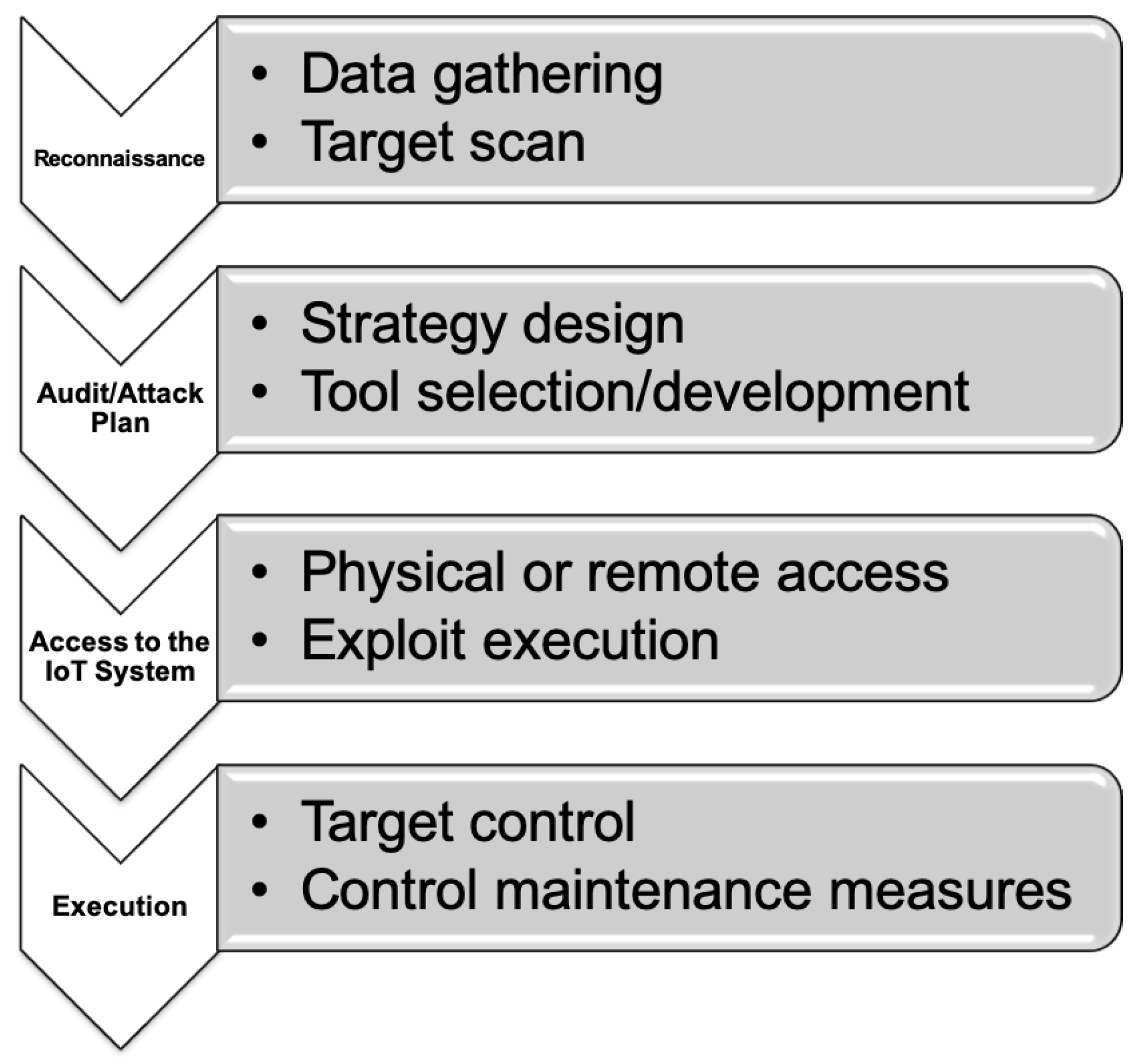
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases

PDF) Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
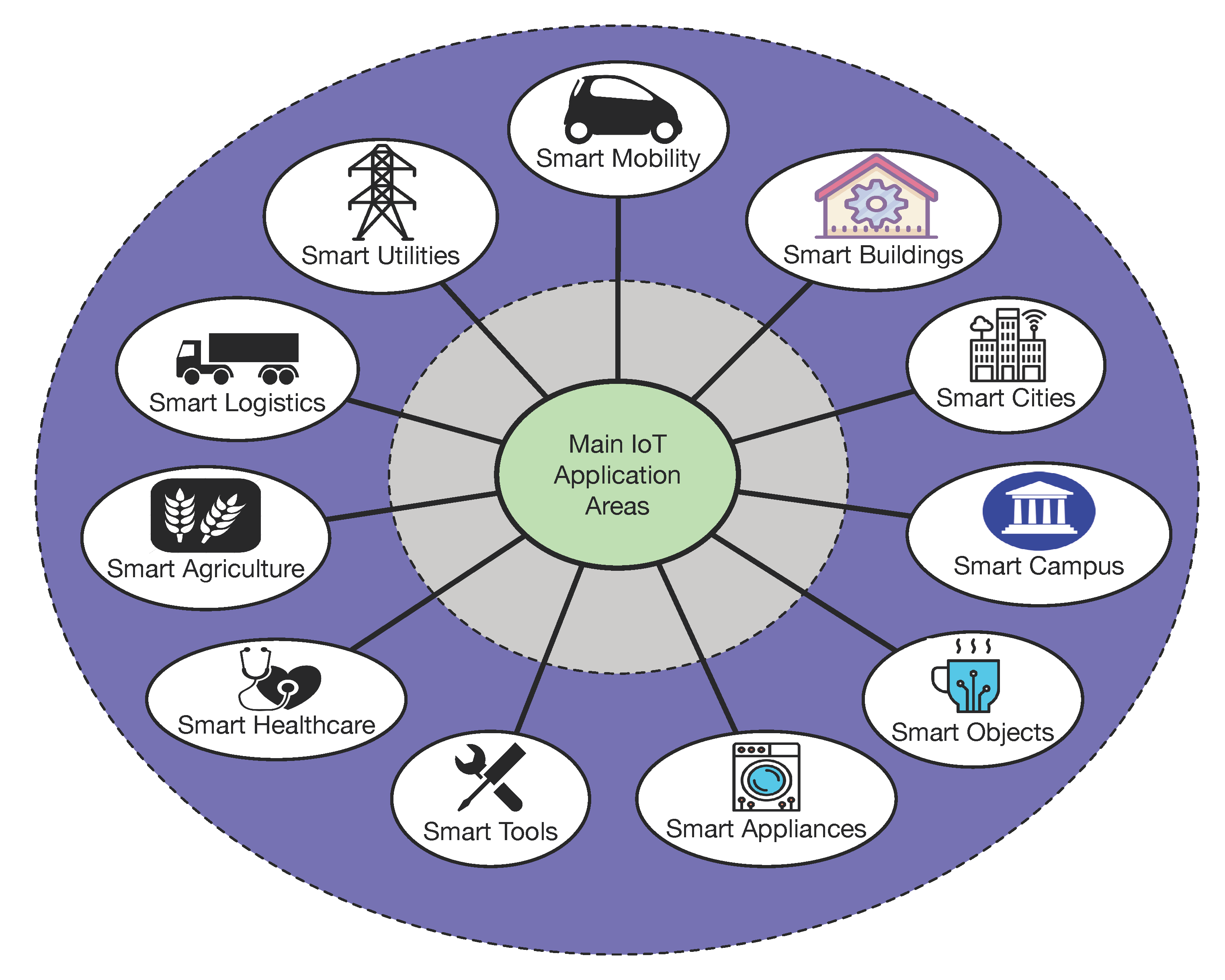
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
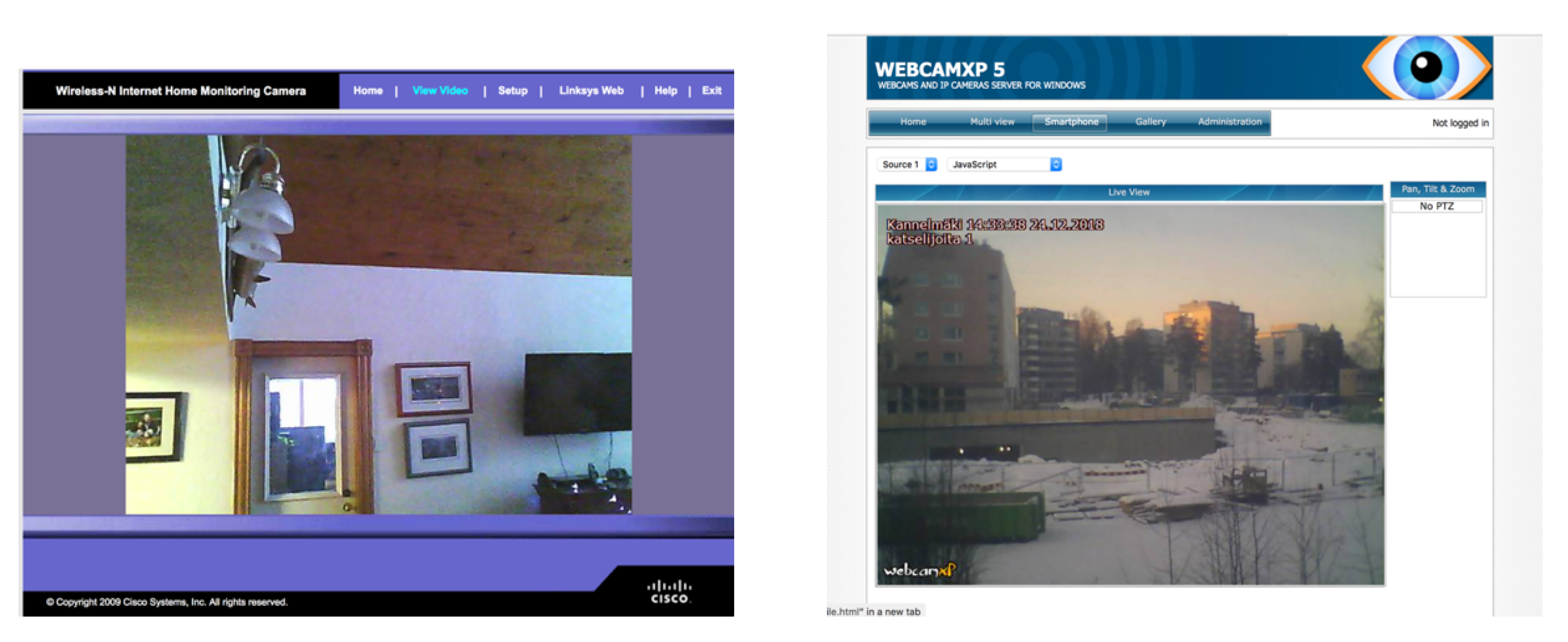
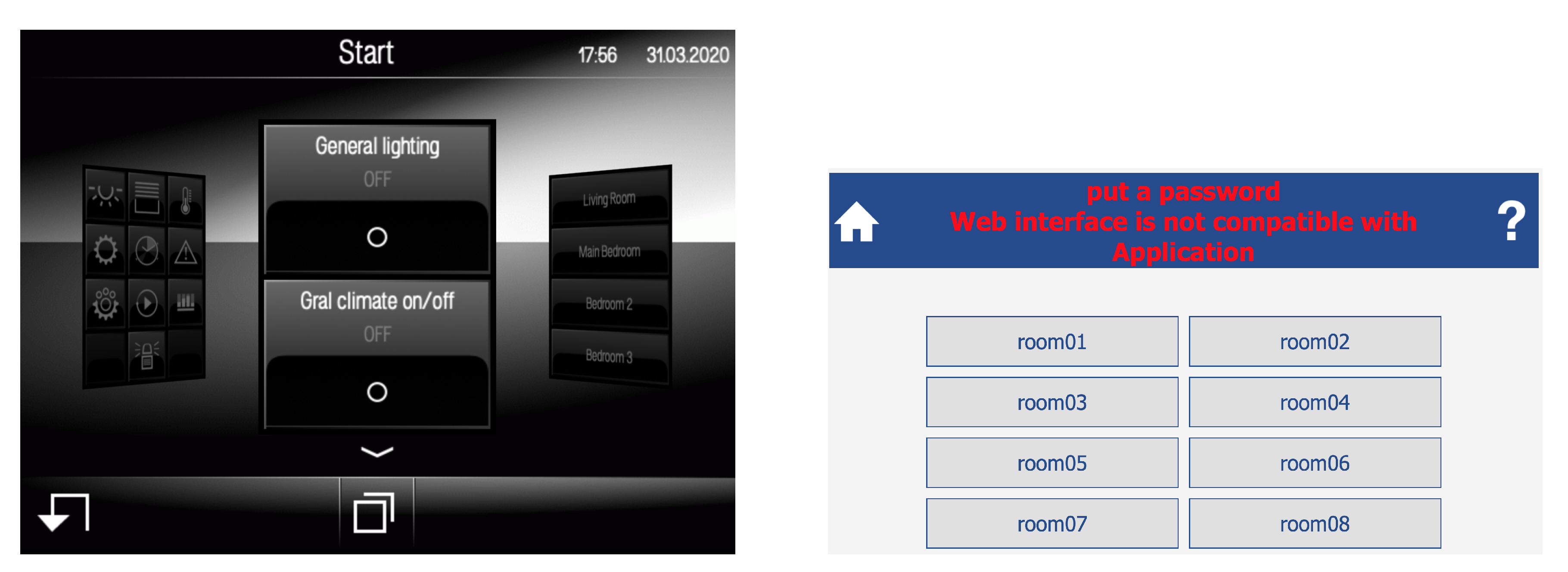
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
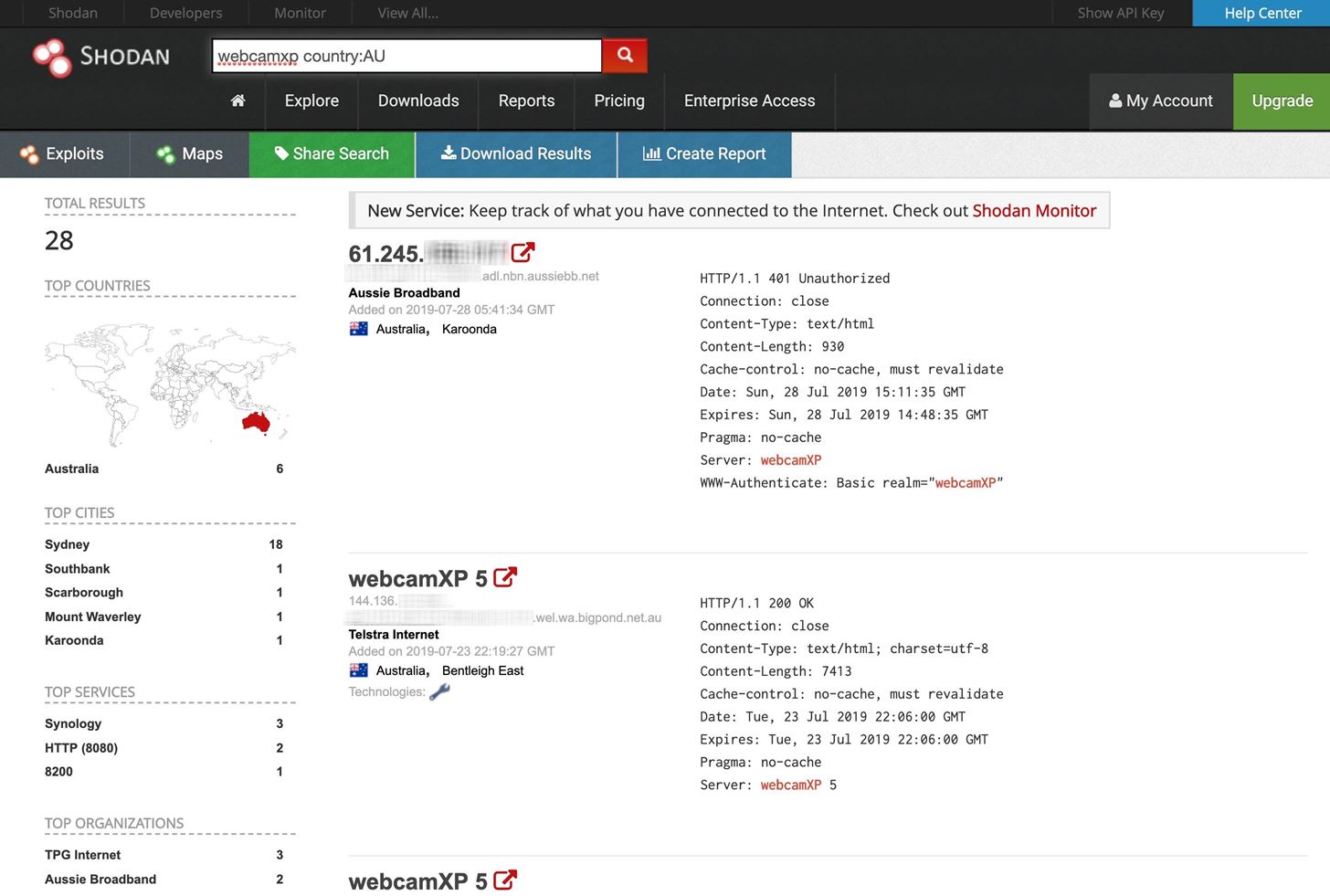
![What Is Shodan? How to Use It & How to Stay Protected [2023] What Is Shodan? How to Use It & How to Stay Protected [2023]](https://static.safetydetectives.com/wp-content/uploads/2019/06/What-is-Shodan-and-how-to-use-it-Most_Effectively.jpg)


![Shodan, cómo evitar que tu webcam y dispositivos IoT sean hackeados [Actualizado] Shodan, cómo evitar que tu webcam y dispositivos IoT sean hackeados [Actualizado]](https://santandergto.com/wp-content/uploads/2019/06/shodan-unsecured-webcam.jpg)