Building secure systems with PII Data Protection Techniques — Part I | by priyadarshan patil | inspiringbrilliance | Feb, 2023 | Medium

Why Should You Tokenize Sensitive Data Like PII, Credit Card? - Strac - Detect & Mask Sensitive Personal Data

Towards A Tokenized Data World: A New World Is Being Created | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

De-identification and re-identification of PII in large-scale datasets using Cloud DLP | Cloud Architecture Center | Google Cloud
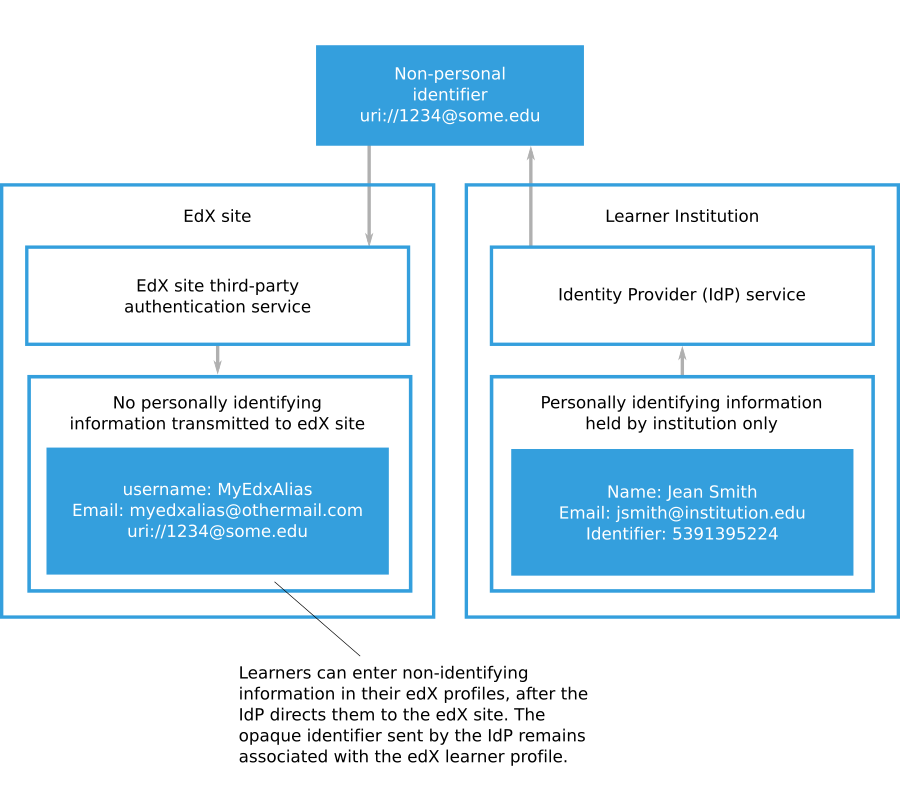
4.23.6. Eliminating PII From Third-Party Authentication — Installing, Configuring, and Running the Open edX Platform documentation





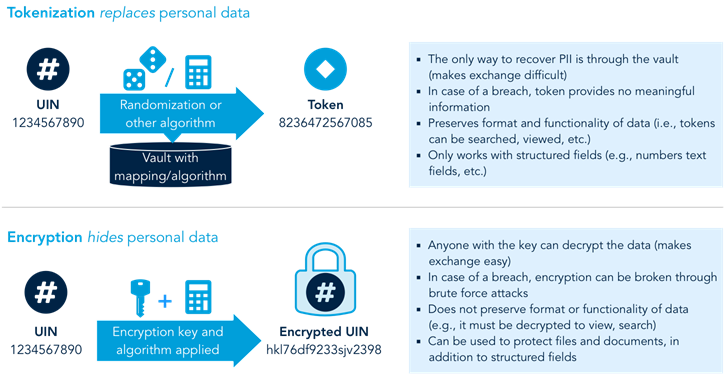

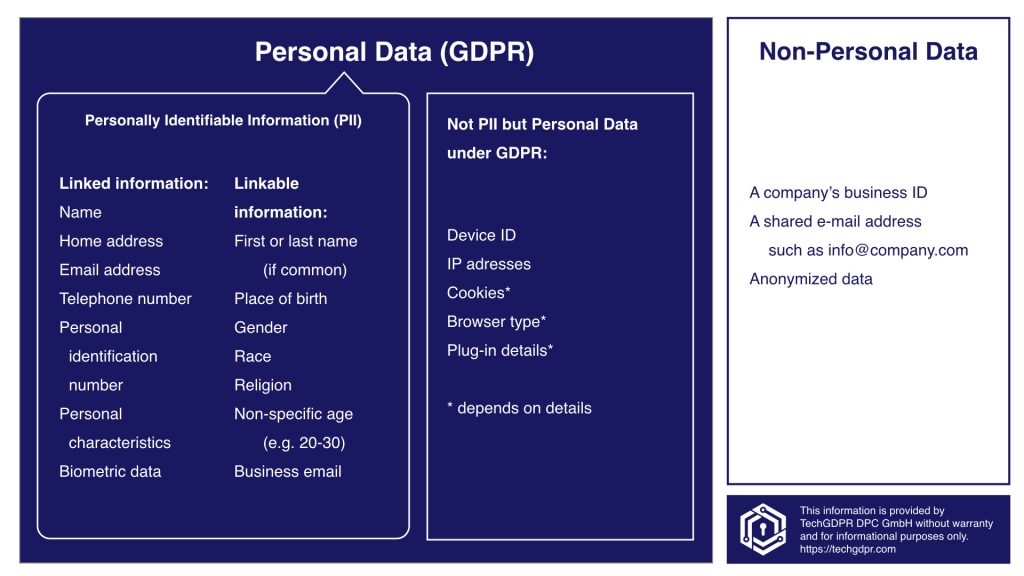
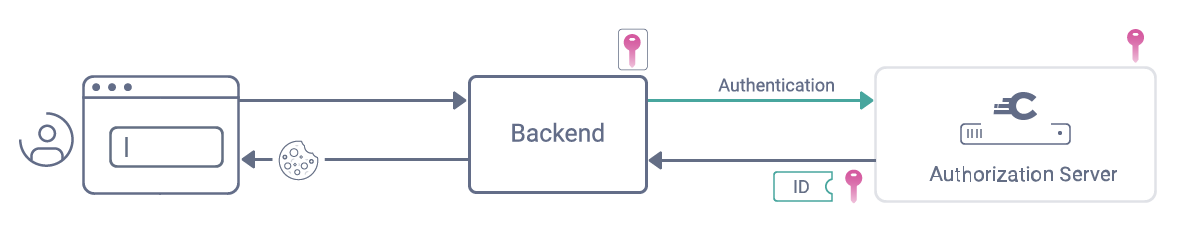
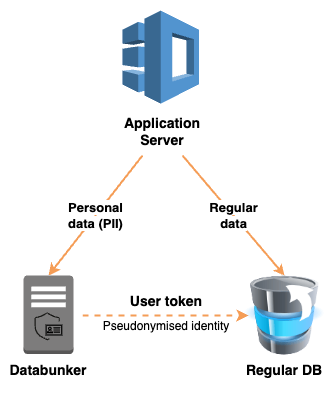
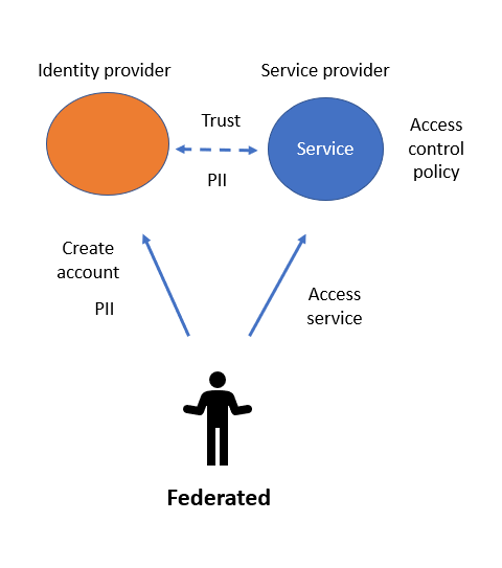



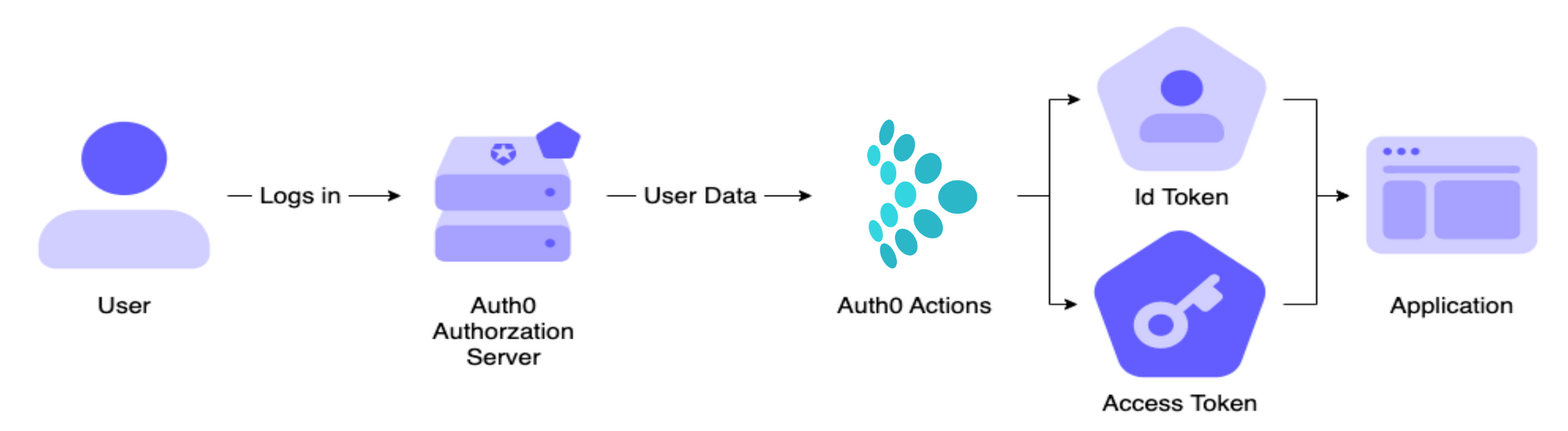

.jpeg)